Toggle a Pixel
Toggle one pixel to make this equality correct.

(71+1)×(71-1) = 7×6×…×2×1 = 7!
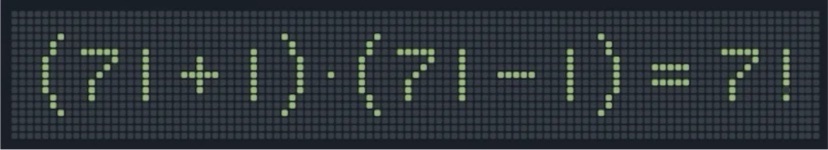
Toggle one pixel to make this equality correct.

(71+1)×(71-1) = 7×6×…×2×1 = 7!

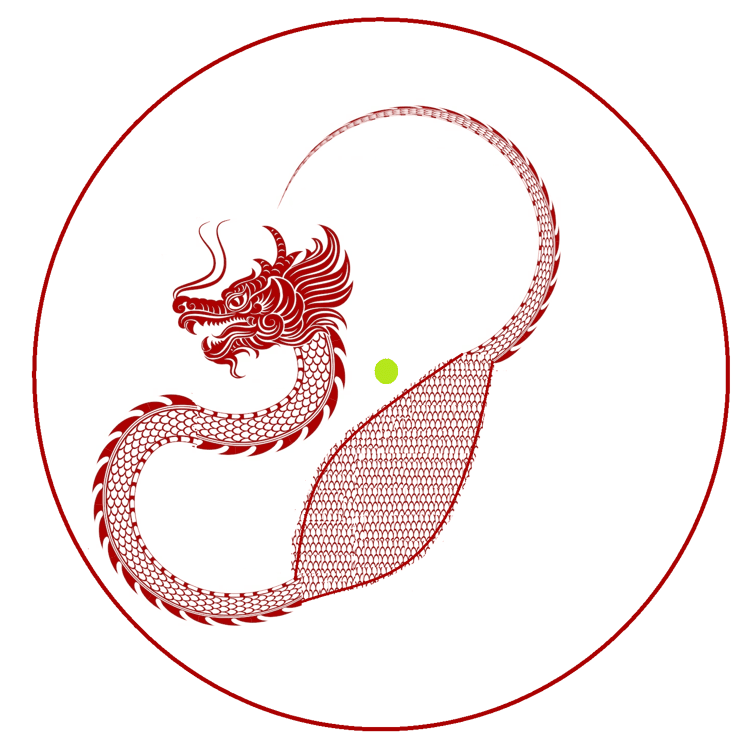
Divide the circle below in two pieces. Then, put the pieces together to get a circle with a dragon, such that the dragon’s eye is at the center of the new circle.
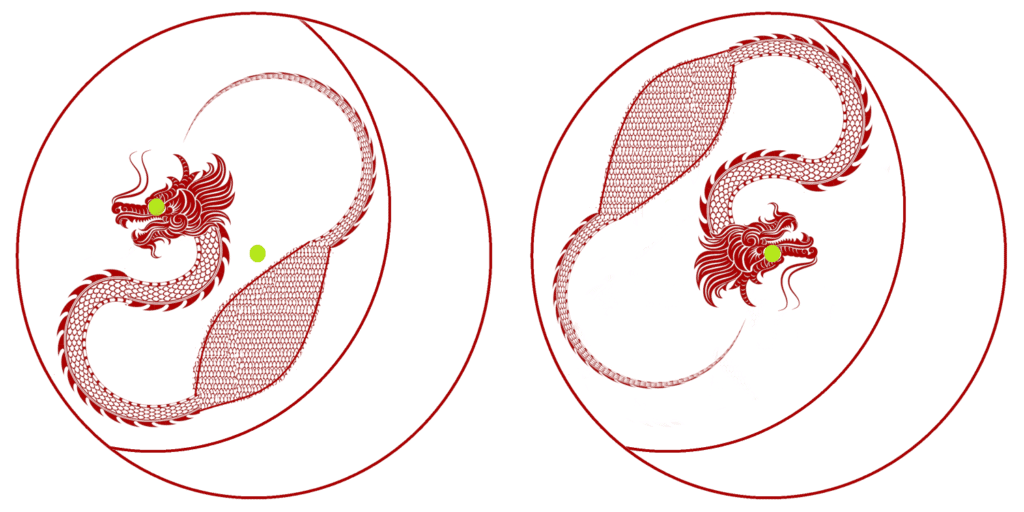
The solution is shown below.
You are sitting on a plane. There is a horse in front of you and a car behind you. Where are you?
You are on a merry-go-round in an amusement park.
Move one red ball to turn the sequence 1-2-3-4 into 4-3-2-1.

Take the second-to-last ball and place it between the first two balls on the left.

Why despite killing dozens of people Charley and Wilma were not punished?
Charley and Wilma were intense hurricanes which formed in August 2004 and October 2005 respectively.
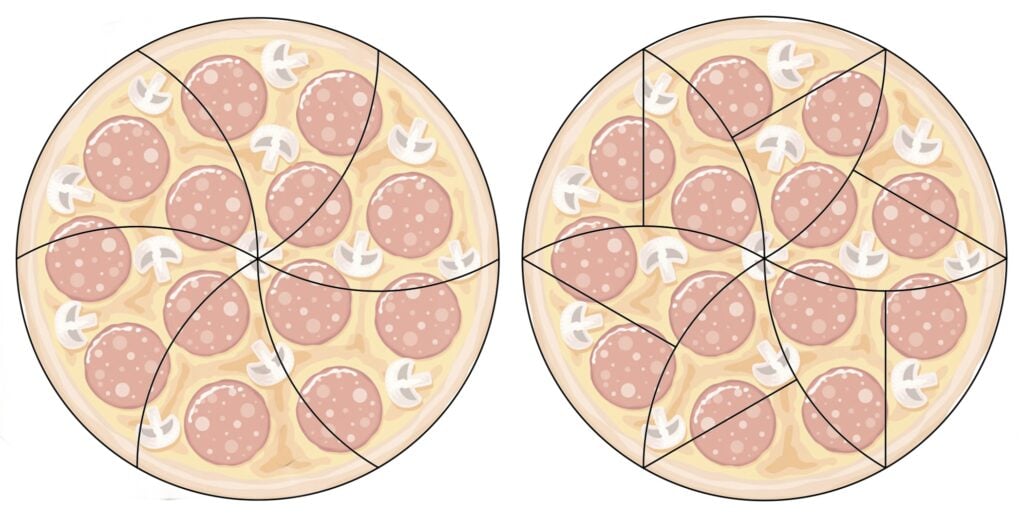
Cut a circular pizza into 12 congruent slices, such that exactly half of them contain crust.
Remark: We say that a slice contains crust if it shares an arc with the boundary of the pizza (with non-zero measure).
First, cut the pizza into 6 congruent circular triangles, and then split each of them in half, as shown on the image below.
White to play. Is this game a win for White, Black, or a draw?
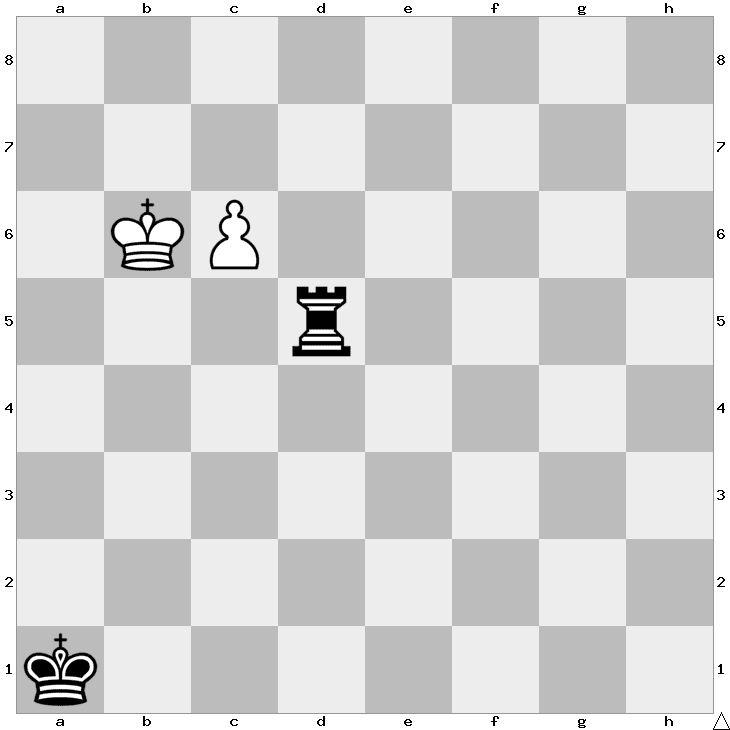
This game is a win for White.
1. c7 Rd6+
2. Kb5 Rd5+
3. Kb4 Rd4+
4. Kb3 Rd3+
5. Kc2! Rd4!
6. c8=R! Ra4
7. Kb3
Now Black will either lose the rook, or get mated in one. If White promoted a Queen instead of a Rook, then 6… Rc4+ would lead to 7. Qxc4, which is a stalemate.
What wears a crown but is no Prince,
Is good at standing but cannot sit,
Digs for years but leaves no pit,
And wears its jewels inside of it?
The answer is TREE.
If you turn the handle of the top left gear clockwise, will the box in the bottom right open or close?
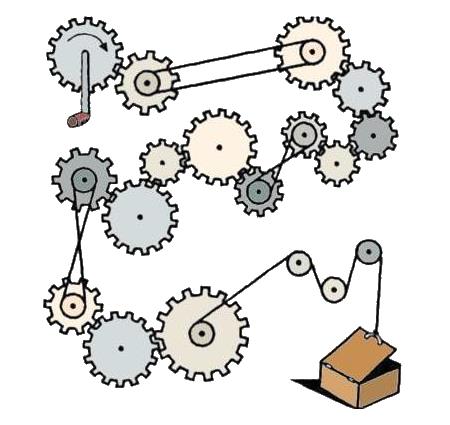
The box will open.
Please confirm you want to block this member.
You will no longer be able to:
Please allow a few minutes for this process to complete.